Maxwell Pro: Network Emulation & Testing
Confidently deploy network based applications and devices.
Maxwell Pro C and P front view
Maxwell Pro C and P rear view
Model C (smaller) and Model P (larger)
Efficient and Reliable Network Emulator Software
Reliably replicate real-world network conditions to optimize app and device performance before product release. Maxwell Pro emulates mobile, cloud and WAN networks, recreating all real-world adverse network conditions like network congestion, slow links, time outs, and other adverse network conditions.
Efficiently and accurately identify performance issues. Proactively address errors to ensure your customers have a solid experience when they get your hardware or software in their hands.
Choose from pre-built test scenarios, or build your own!
Inject any network, protocol, or packet level impairment
Graphic, command line or script driven interface
Fully programmable in C, C++, or Python
Support for 10 GbE interfaces
Discover Application Problems, Before They Become Problems
Test, diagnose and remediate application performance in new releases by replicating the production network in the lab.
Detect and track individual flows while remaining undetectable to other devices on the network.
Intelligently test thousands of code paths, not just the most common paths, in a stateful manner.
Simplify rigorous, repeatable, regression testing.
Multiple flows and stateful operation.
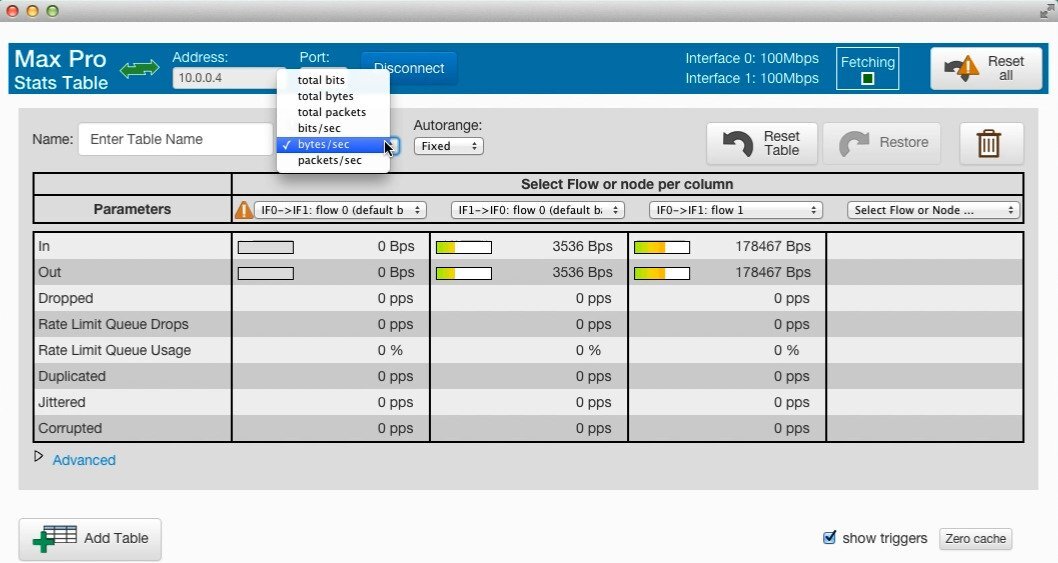
Greater granularity and fidelity when emulating real-world networks
Discover problems earlier, fix them, and release higher-quality products and applications.
With Maxwell Pro's powerful network emulator software, you can achieve greater granularity and fidelity when emulating real-world networks, allowing you to discover and address problems early in the development process. By simulating a wide range of network technologies and applications, such as VoIP, video conferencing, SANs, wireless, mobile, and VPN, Maxwell Pro offers extensive capabilities to ensure the quality and performance of your products and applications.
Maxwell Pro's flexible, scriptable, programmable power enables an abundance of capabilities
Simulate all network technologies and applications, including VoIP, video conferencing, SANs, wireless, mobile, VPN, and many more with Maxwell Pro.
Add time-varying impairments to your emulation
Real world networks change their behavior over time. And so should your network emulation scenario.
Create a network emulation that varies the impairment parameters over any time period
Specify a time-varying expression for any metric, using equations, piecewise curves, or shaped pulses
We looked at a number of products, but selected Maxwell because of the ability to create custom impairments and custom filters. This is very useful in our testing environment.
Engineering Manager, Thomson Technology
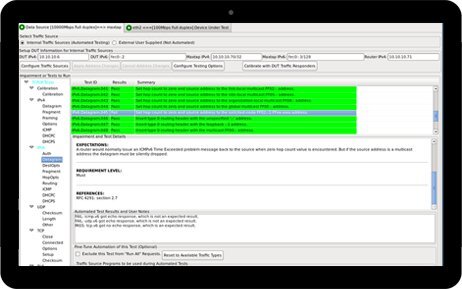
Protocol testing with Maxwell Pro
Maxwell Pro is a hardware solution that offers the addition of protocol test suites to help quality assurance engineers find bug in their network protocol stacks.
DHCP
ICMP
IP
SIP
TCP
UDP
Test multimedia G.1050
The ITU-T Recommendation G.1050 provides a standardized network model for evaluating multimedia transmission performance over the internet. Maxwell Pro's G.1050 tests help product manufacturers verify proper device performance under a range of known, deployed network configurations including common network anomalies and impairments. Validate application performance and guarantee the success of your cloud-based initiative with pre-deployment testing.
With Maxwell Pro you can test:
Storage in the cloud applications under limited bandwidth connections
Audio interaction over the internet for gaming applications
Multimedia devices containing video, voice streams & more
Compare IWL Network Emulators
Need More Technical Information?
Maxwell Pro Vs. Brand X
White Papers
Understanding How Applications Perform on the Network — Even Under Adverse Network Conditions
Read MoreEmulating Mobile/Cellular Networks
Read MoreRate Limitation vs. Bandwidth Limitation
Read MoreCauses and Correlation of Network Impairments
Read MoreLimitations of ICMP Echo for network measurement
Read MoreNetwork Emulation Executive Overview
Read More
Use Cases
Counting Bits - Measuring Network Data Rates
Read MorePerformance Testing an IoT Device
Read MoreNetwork Emulation in the Lab vs. Real World Network Testing
Read MoreFive Best Practices to Avoid Data Center Relocation Disaster
Read MoreIs Network Latency Affecting Your Business' Cloud Performance?
Read More
Videos
Complete list of Maxwell Pro TCP/IP videos: Watch Videos
The Maxwell Pro TCP/IP videos include:
Why Your Cruise Ship Internet is So Slow (and what can be done about it)
Using Maxwell Fluctuations (waveforms)
Testing your Device with the Maxwell Pro TCP/IP Test Suite